StealC - Analysis :
DIE :


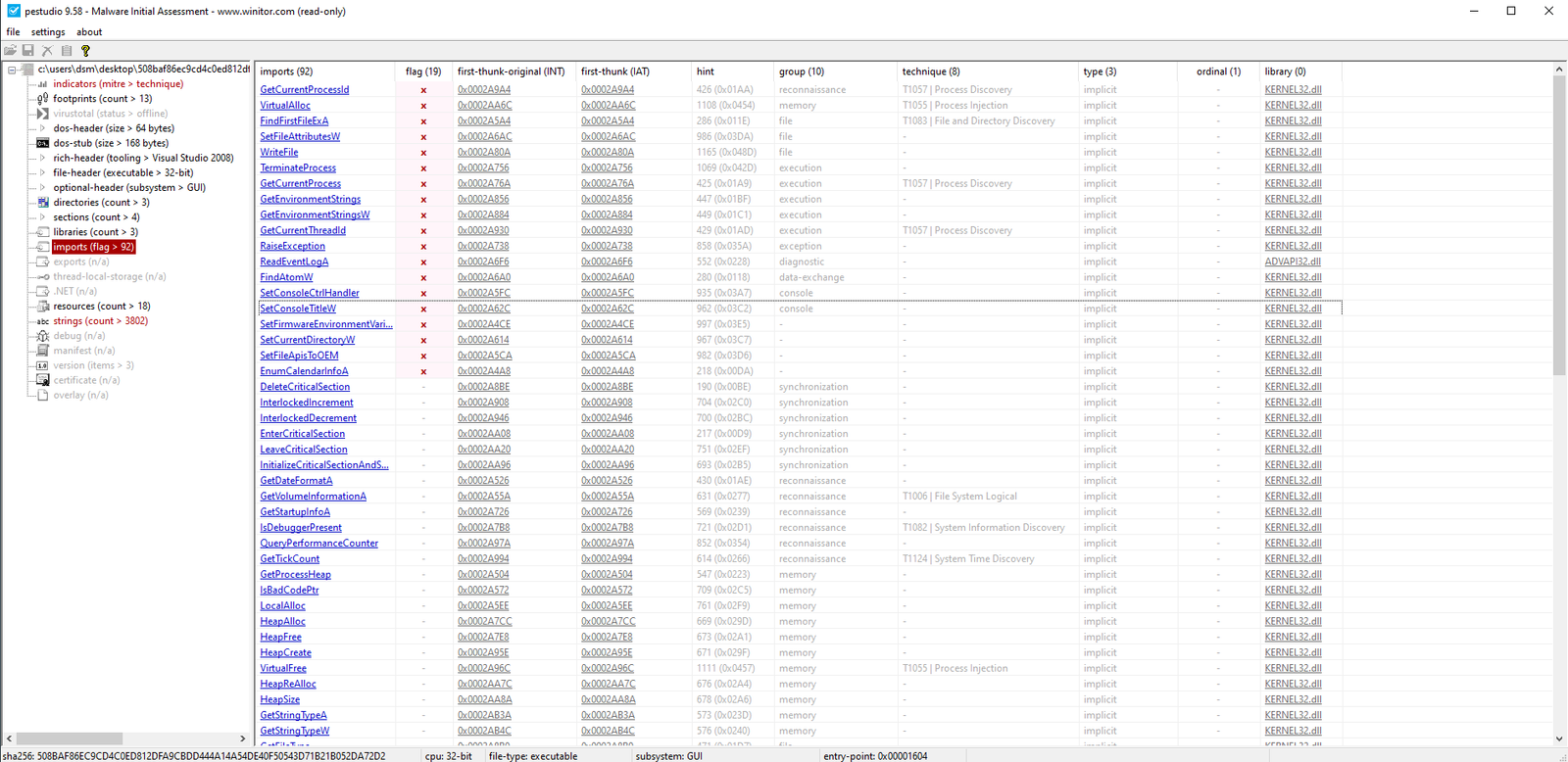
PEStudio :

Binja :
trying to get the unpacked version





trying to get the unpacked version


┍━━━━━━━━━━━━━━━━━━━━━━━━┯━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┑
│ md5 │ 0e1cddca920547a1721fd6621c8c84cd │
│ sha1 │ 1268f12d671f23416ad5fc968cc54f11a8e1533f │
│ sha256 │ c2d25d9c88f68286f332ee1b0e989046c28bf5f10383990b5dcbb7d639ee21bc │
│ analysis │ static │
│ os │ any │
│ format │ pe │
│ arch │ i386 │
│ path │ C:/Users/DsM/Desktop/c2d25d9c88f68286f332ee1b0e989046c28bf5f10383990b5dcbb7d639ee21bc.exe │
┕━━━━━━━━━━━━━━━━━━━━━━━━┷━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┙
┍━━━━━━━━━━━━━━━━━━━━━━━━┯━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┑
│ ATT&CK Tactic │ ATT&CK Technique │
┝━━━━━━━━━━━━━━━━━━━━━━━━┿━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┥
│ DEFENSE EVASION │ Deobfuscate/Decode Files or Information T1140 │
│ │ Modify Registry T1112 │
│ │ Obfuscated Files or Information T1027 │
│ │ Process Injection::Thread Execution Hijacking T1055.003 │
│ │ Reflective Code Loading T1620 │
│ │ Virtualization/Sandbox Evasion::System Checks T1497.001 │
├────────────────────────┼────────────────────────────────────────────────────────────────────────────────────┤
│ DISCOVERY │ Account Discovery T1087 │
│ │ File and Directory Discovery T1083 │
│ │ Process Discovery T1057 │
│ │ Query Registry T1012 │
│ │ System Information Discovery T1082 │
│ │ System Owner/User Discovery T1033 │
├────────────────────────┼────────────────────────────────────────────────────────────────────────────────────┤
│ EXECUTION │ Windows Management Instrumentation T1047 │
┕━━━━━━━━━━━━━━━━━━━━━━━━┷━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┙
┍━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┯━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┑
│ MBC Objective │ MBC Behavior │
┝━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┿━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┥
│ ANTI-BEHAVIORAL ANALYSIS │ Virtual Machine Detection [B0009] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ COMMAND AND CONTROL │ C2 Communication::Receive Data [B0030.002] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ COMMUNICATION │ HTTP Communication::Get Response [C0002.017] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ CRYPTOGRAPHY │ Generate Pseudo-random Sequence::Use API [C0021.003] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ DATA │ Decode Data::Base64 [C0053.001] │
│ │ Encode Data::Base64 [C0026.001] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ DEFENSE EVASION │ Obfuscated Files or Information::Encoding-Standard Algorithm [E1027.m02] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ DISCOVERY │ File and Directory Discovery [E1083] │
│ │ System Information Discovery [E1082] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ MEMORY │ Allocate Memory [C0007] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ OPERATING SYSTEM │ Environment Variable::Set Variable [C0034.001] │
│ │ Registry::Delete Registry Value [C0036.007] │
│ │ Registry::Query Registry Key [C0036.005] │
│ │ Registry::Query Registry Value [C0036.006] │
│ │ Registry::Set Registry Key [C0036.001] │
├─────────────────────────────┼───────────────────────────────────────────────────────────────────────────────┤
│ PROCESS │ Create Process [C0017] │
│ │ Create Thread [C0038] │
│ │ Suspend Thread [C0055] │
│ │ Terminate Process [C0018] │
┕━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┷━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┙
┍━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┯━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┑
│ Capability │ Namespace │
┝━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┿━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┥
│ reference anti-VM strings targeting Qemu │ anti-analysis/anti-vm/vm-detection │
│ receive data │ communication │
│ decode data using Base64 in .NET (15 matches) │ data-manipulation/encoding/base64 │
│ encode data using Base64 (3 matches) │ data-manipulation/encoding/base64 │
│ generate random numbers in .NET (2 matches) │ data-manipulation/prng │
│ find data using regex in .NET (2 matches) │ data-manipulation/regex │
│ contains PDB path │ executable/pe/pdb │
│ access .NET resource │ executable/resource │
│ set environment variable │ host-interaction/environment-variable │
│ get common file path │ host-interaction/file-system │
│ check if directory exists │ host-interaction/file-system/exists │
│ manipulate unmanaged memory in .NET │ host-interaction/memory │
│ get hostname (2 matches) │ host-interaction/os/hostname │
│ get OS version in .NET │ host-interaction/os/version │
│ create process on Windows │ host-interaction/process/create │
│ inject thread │ host-interaction/process/inject │
│ find process by PID │ host-interaction/process/list │
│ find process by name (2 matches) │ host-interaction/process/list │
│ terminate process (2 matches) │ host-interaction/process/terminate │
│ terminate process by name in .NET │ host-interaction/process/terminate │
│ query or enumerate registry key (2 matches) │ host-interaction/registry │
│ query or enumerate registry value │ host-interaction/registry │
│ set registry value │ host-interaction/registry/create │
│ delete registry value │ host-interaction/registry/delete │
│ get session user name │ host-interaction/session │
│ suspend thread (5 matches) │ host-interaction/thread/suspend │
│ access WMI data in .NET │ host-interaction/wmi │
│ spawn thread to RWX shellcode │ load-code/shellcode │
│ unmanaged call (5 matches) │ runtime │
│ compiled to the .NET platform │ runtime/dotnet │
┕━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┷━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┙
output en json : ![[res.json]]